ADVISORY!
TLP : CLEAR
Date : 13/09/2024
REF NO : CERT / 2024/09/82
Multiple Vulnerabilities in Siemens Products
Severity Level: High
Components Affected
- SIMATIC Information Server 2022 & 2024
- SIMATIC PCS neo all versions V4.0, prior to V4.1 and V5.0
- SINEC NMS all versions prior to V2.11.6
- Totally Integrated Automation Portal (TIA Portal) all versions V16, prior to V17 Update 8, V18 & V19
- Mendix Runtime V8 all versions, V9 all versions prior to V9.24.26, V10 all versions prior to V10.14.0,V10.6 all versions prior to V10.6.12, V10.12 all versions prior to V10.6.12 & V10.12.2
- SINUMERIK 828D V4 & SINUMERIK 840D sl V4 All versions prior to V4.95 SP3
- SINUMERIK ONE All versions prior to V6.23 & V6.15 SP4
- Automation License Manager All versions V5, V6.0 and V6.2 All versions prior to V6.2 Upd3
- SINUMERIK 828D V4, SINUMERIK 840D sl V4 all versions & SINUMERIK 828D V5 all versions prior to V5.24
- SINUMERIK ONE All versions prior to V6.24
- Industrial Edge Management Pro All versions prior to V1.9.5
- Industrial Edge Management Virtual All versions prior to V2.3.1-1
- SINEMA Remote Connect Client All versions prior to V3.2 SP2
- SIMATIC CP 1242-7 V2, SIMATIC CP 1243-1, DNP3, IEC (incl. SIPLUS variants) All versions prior to V3.5.20
- SIMATIC CP 1243-7 LTE & SIMATIC CP 1243-8 IRC (6GK7243-8RX30-0XE0) All versions prior to V3.5.20
- SIMATIC HMI Comfort Panels (incl. SIPLUS variants) All versions
- SIMATIC IPC DiagBase, DiagMonitor & SIMATIC WinCC Runtime Advanced All versions
- SIPLUS TIM 1531 IRC (6AG1543-1MX00-7XE0) & TIM 1531 IRC (6GK7543-1MX00-0XE0) All versions prior to V2.4.8
- Tecnomatix Plant Simulation V2302 All versions prior to V2302.0015
- Tecnomatix Plant Simulation V2404 All versions prior to V2404.0004
- Industrial Edge Management OS (IEM-OS) All versions
- SINEMA Remote Connect Server All versions prior to V3.2 SP2
- SINUMERIK ONE All versions prior to V6.24
- ETI5 Ethernet Int. 1x100TX IEC61850 All versions prior to V05.30
- SICAM SCC All versions prior to V10.0
- SITIPE AT All versions
- SCALANCE W-700 IEEE 802.11ax family prior to V2.4.0
- AI Model Deployer All versions prior to V1.1
- Data Flow Monitoring Industrial Edge Device User Interface (DFM IED UI) All versions prior to V0.0.6
- LiveTwin Industrial Edge app (6AV2170-0BL00-0AA0) All versions prior to V2.4
- SIMATIC PCS neo V4.1 All versions prior to V4.1 Update 2 & neo V5.0 All versions
- SIMATIC WinCC Runtime Professional All versions V18, V19, V20
- SIMATIC WinCC V7.4 All versions with installed WebRH, WinCC V7.5 & V8.0
- TIA Administrator All versions prior to V3.0 SP3
- SIMATIC S7-200 SMART CPU family all versions
- SIMATIC RFID Readers
Overview
Multiple vulnerabilities have been reported in Siemens products which could allow an attacker to execute arbitrary code, gain elevated privileges, obtain sensitive Information and cause denial of service (DoS) conditions or perform Man-In-The-Middle (MitM) attack on the targeted system.
Description
Multiple vulnerabilities have been reported in various Siemens products; details of which are provided below:
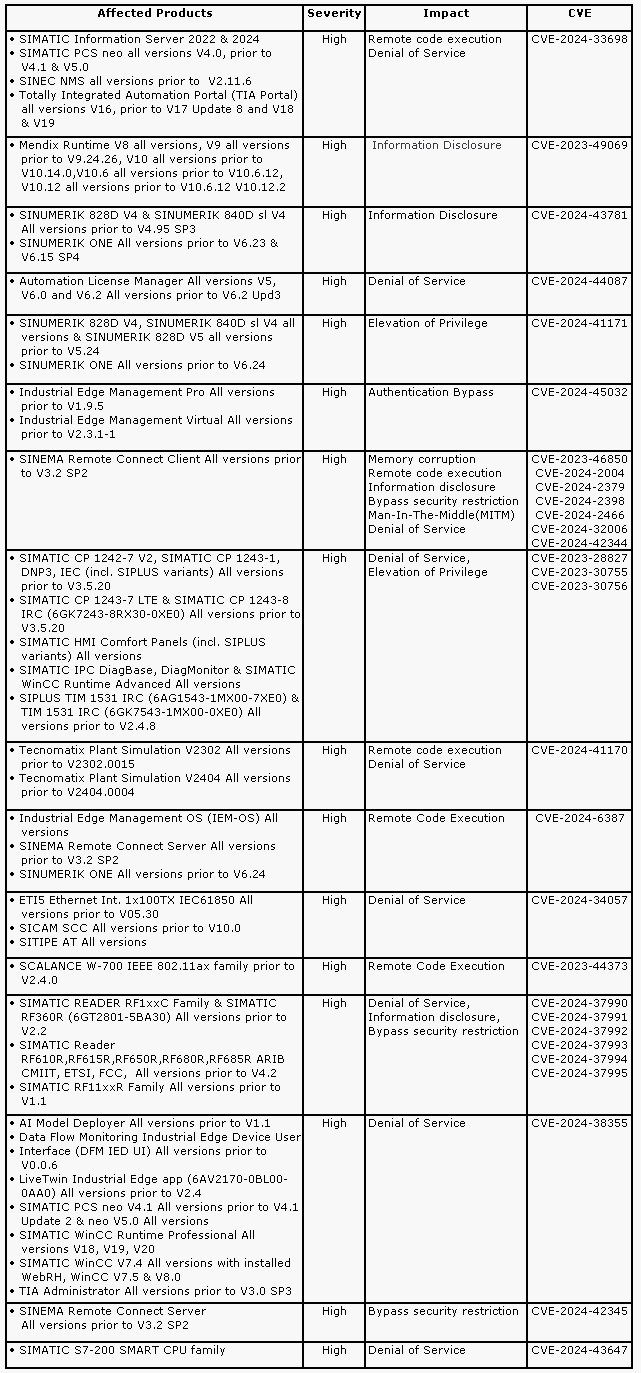
Impact
- Remote code execution
- Denial of service
- Information Disclosure
- Elevation of Privilege
- Authentication Bypass
- Memory corruption
- Bypass security restriction
- Man-In-The-Middle (MITM)
Solution/ Workarounds
Apply appropriate security updates as mentioned in Siemens Security Advisory:
https://www.siemens.com/global/en/products/services/cert.html#SiemensSecurityAdvisories
Reference
- https://cert-portal.siemens.com/productcert/html/ssa-969738.html
- https://cert-portal.siemens.com/productcert/html/ssa-869574.html
- https://cert-portal.siemens.com/productcert/html/ssa-773256.html
- https://cert-portal.siemens.com/productcert/html/ssa-765405.html
- https://cert-portal.siemens.com/productcert/html/ssa-721642.html
- https://cert-portal.siemens.com/productcert/html/ssa-673996.html
- https://cert-portal.siemens.com/productcert/html/ssa-446545.html
- https://cert-portal.siemens.com/productcert/html/ssa-427715.html
- https://cert-portal.siemens.com/productcert/html/ssa-423808.html
- https://cert-portal.siemens.com/productcert/html/ssa-417159.html
- https://cert-portal.siemens.com/productcert/html/ssa-359713.html
- https://cert-portal.siemens.com/productcert/html/ssa-342438.html
- https://cert-portal.siemens.com/productcert/html/ssa-103653.html
- https://cert-portal.siemens.com/productcert/html/ssa-097786.html
- https://cert-portal.siemens.com/productcert/html/ssa-097435.html
- https://cert-portal.siemens.com/productcert/html/ssa-039007.html
Disclaimer : The information provided herein is on an “as is” basis, without warranty of any kind.
Sri Lanka Computer Emergency Readiness Team | Coordination Centre
- Hotline : 101
- +94 11 269 1692
- Room 4-112, BMICH, Bauddhaloka Mawatha, Colombo 07, Sri Lanka.
- General inquiry: cert@cert.gov.lk
- Security incidents: incidents@cert.gov.lk
- Social media incidents: report@cert.gov.lk



