ADVISORY!
TLP : CLEAR
Date : 16/02/2024
REF NO : CERT / 2024/02/13
Microsoft Products Multiple Vulnerabilities
Severity Level: High
Components Affected
- Browser
- Azure
- Developer Tools
- Windows
- Extended Security Updates (ESU)
- Microsoft Dynamics
- Microsoft Office
- System Center
- Exchange Server
- Mariner
Overview
Exploit in the wild has been detected for CVE-2024-21410, affecting Microsoft Exchange Server. The vulnerability could be exploited by sending a crafted request to steal user’s NTLM hash.
Proof of Concept exploit code is publicly available for CVE-2024-21413, affecting Microsoft Outlook. The vulnerability could be exploited by clicking on a malicious URL and execute arbitrary code.
Description
| Vulnerable Product | Risk Level | Impacts | Notes |
| Browser |  Medium Risk Medium Risk | Remote Code Execution | |
| Azure |  Medium Risk Medium Risk | Remote Code Execution Elevation of Privilege Spoofing | |
| Developer Tools |  Medium Risk Medium Risk | Remote Code Execution Denial of Service | |
| Windows |  Medium Risk Medium Risk | Denial of Service Elevation of Privilege Information Disclosure Remote Code Execution Security Restriction Bypass Spoofing | CVE-2024-21351 is being exploited in the wild. The vulnerability allows a malicious actor to inject code into SmartScreen and potentially gain code execution, which could potentially lead to some data exposure, lack of system availability, or both.
CVE-2024-21412 is being exploited in the wild. The vulnerability could bypass Mark of the Web (MoTW) warnings in Windows. |
| Extended Security Updates (ESU) |  Medium Risk Medium Risk | Denial of Service Information Disclosure Remote Code Execution Elevation of Privilege Spoofing | |
| Microsoft Dynamics |  Medium Risk Medium Risk | Spoofing Information Disclosure | |
| Microsoft Office | 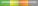 High Risk High Risk | Remote Code Execution Elevation of Privilege Information Disclosure | [Updated on 2024-02-16] CVE-2024-21413 Proof-Of-Concept is available in public. The vulnerability could be exploited by clicking a malicious URL and execute arbitrary code. |
| System Center |  Medium Risk Medium Risk | Elevation of Privilege | |
| Exchange Server | 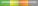 High Risk High Risk | Elevation of Privilege | [Updated on 2024-02-16] CVE-2024-21410 is being exploited in the wild. The vulnerability could be exploited by sending a crafted request to steal user’s NTLM hash. |
| Mariner | 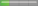 Low Risk Low Risk |
Impact
- Remote Code Execution
- Security Restriction Bypass
- Elevation of Privilege
- Denial of Service
- Information Disclosure
- Spoofing
Solution/ Workarounds
Before installation of the software, please visit the vendor web-site for more details.
- Apply fixes issued by the vendor.
Reference
- https://learn.microsoft.com/en-us/previous-versions/dn602597(v=msdn.10)?redirectedfrom=MSDN
- https://www.cvedetails.com/vulnerability-list/vendor_id-26/Microsoft.html?page=1&year=2024&month=2&order=1&trc=73&sha=2822b912461e35f80797af020b1d3663b30cb096
- https://msrc.microsoft.com/update-guide/releaseNote/2024-Feb
Disclaimer : The information provided herein is on an “as is” basis, without warranty of any kind.
Sri Lanka Computer Emergency Readiness Team | Coordination Centre
- Hotline : 101
- +94 11 269 1692
- Room 4-112, BMICH, Bauddhaloka Mawatha, Colombo 07, Sri Lanka.
- General inquiry: cert@cert.gov.lk
- Security incidents: incidents@cert.gov.lk
- Social media incidents: report@cert.gov.lk



