ADVISORY!
TLP : CLEAR
Date : 28/08/2024
REF NO : CERT / 2024/08/77
Multiple Vulnerabilities in Siemens Products
Severity Level: High
Components Affected
- Siemens SCALANCE M-800 family Versions prior to V8.1
- Siemens NX All versions prior to V2406.3000
- Siemens INTRALOG WMS All versions prior to V4
- Siemens COMOS All versions prior to V10.5
- Siemens SINEC Traffic Analyzer (6GK8822-1BG01-0BA0) All versions prior to V2.0
- Siemens Location Intelligence family All versions prior to V4.4
- Siemens SINEC NMS All versions prior to V3.0
- Siemens JT2Go All versions prior to V2312.0005
- Siemens Teamcenter Visualization V14.2 All versions prior to V14.2.0.12
- Siemens LOGO! versions prior to V8.3 BM (incl. SIPLUS variants)
Overview
Multiple vulnerabilities have been reported in Siemens Products which could allow an attacker to execute arbitrary code, escalate privileges, bypass security controls, disclose sensitive information or perform denial of service (DoS) condition on the targeted system.
Description
Multiple vulnerabilities have been reported in various Siemens products; details of which are provided below:
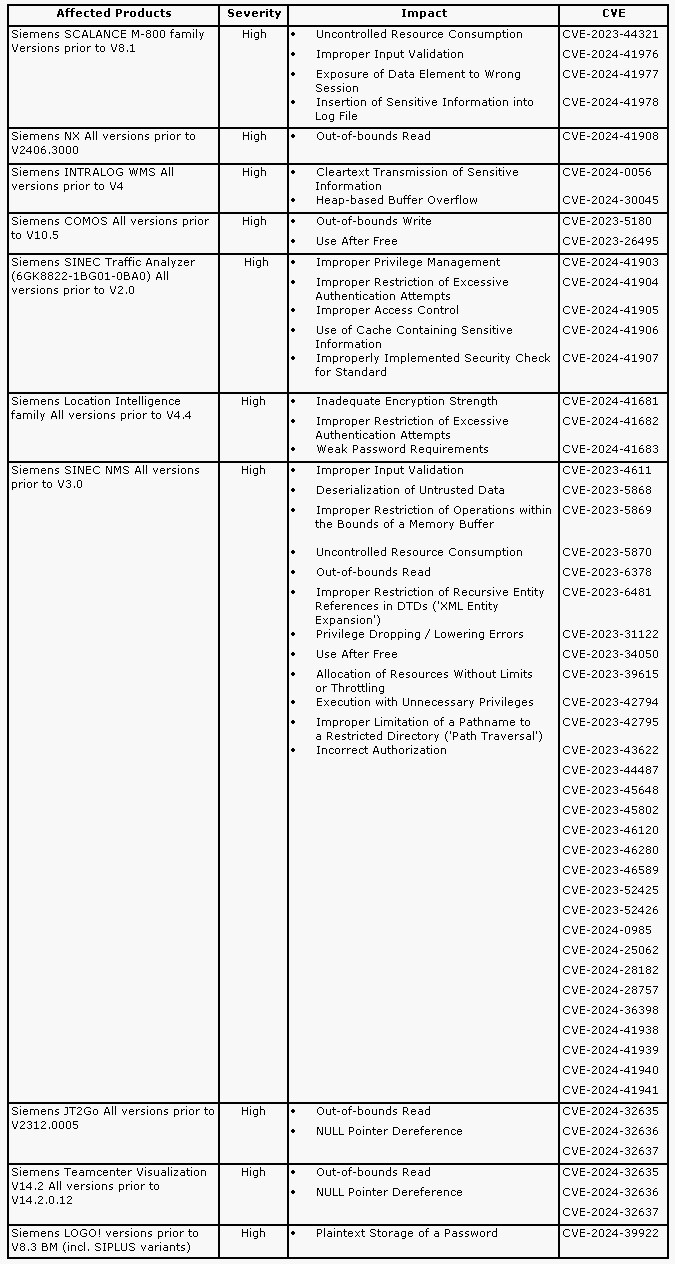
Impact
- Uncontrolled resource consumption
- Improper input validation
- Exposure of data element to wrong session
- Insertion of sensitive information into log file
- Out of bounds read
- Clear text transmission of sensitive information
- Heap based buffer overflow
- Out of bounds write
- Use after free
- Improper restriction of excessive authentication attempts
- Improper privilege management
- Improper access control
- Use of cache containing sensitive information
- Improperly implemented security check for standard
- Inadequate Encryption strength
- Improper restriction of excessive authentication attempts
- Weak passwords requirements
- Deserialization of untrusted data
- Improper restriction of operations within the bounds of a memory buffer
- Improper restriction of recursive entity references in DTDs
- Privilege dropping
- Allocation of resources without limits or throttling
- Execution with unnecessary privileges
- Improper limitation of a pathname to a Restricted directory
- Incorrect authorization
- NULL pointer dereference
- Plaintext storage of a password
Solution/ Workarounds
Apply appropriate fixes as mentioned in Siemens Security Advisory:
Siemens
https://cert-portal.siemens.com/productcert/html/ssa-921449.html
https://cert-portal.siemens.com/productcert/html/ssa-856475.html
https://cert-portal.siemens.com/productcert/html/ssa-784301.html
https://cert-portal.siemens.com/productcert/html/ssa-720392.html
https://cert-portal.siemens.com/productcert/html/ssa-716317.html
https://cert-portal.siemens.com/productcert/html/ssa-659443.html
https://cert-portal.siemens.com/productcert/html/ssa-417547.html
https://cert-portal.siemens.com/productcert/html/ssa-357412.html
https://cert-portal.siemens.com/productcert/html/ssa-087301.html
Reference
Siemens
- https://cert-portal.siemens.com/productcert/html/ssa-921449.html
- https://cert-portal.siemens.com/productcert/html/ssa-856475.html
- https://cert-portal.siemens.com/productcert/html/ssa-784301.html
- https://cert-portal.siemens.com/productcert/html/ssa-720392.html
- https://cert-portal.siemens.com/productcert/html/ssa-716317.html
- https://cert-portal.siemens.com/productcert/html/ssa-659443.html
- https://cert-portal.siemens.com/productcert/html/ssa-417547.html
- https://cert-portal.siemens.com/productcert/html/ssa-357412.html
- https://cert-portal.siemens.com/productcert/html/ssa-087301.html
Disclaimer : The information provided herein is on an “as is” basis, without warranty of any kind.
Sri Lanka Computer Emergency Readiness Team | Coordination Centre
- Hotline : 101
- +94 11 269 1692
- Room 4-112, BMICH, Bauddhaloka Mawatha, Colombo 07, Sri Lanka.
- General inquiry: cert@cert.gov.lk
- Security incidents: incidents@cert.gov.lk
- Social media incidents: report@cert.gov.lk



