Browser In The Browser (BITB) Attack
Introduction
It’s important to recognize that cyber attackers are constantly devising new methods to trick users into revealing their valuable information, such as credentials and secret keys. These schemes typically target unsuspecting users, regardless of their level of sophistication. The primary detail to focus on in order to avoid phishing is the website address where you’re asked to input your credentials. However, there’s a unique type of attack that operates differently, fooling victims with a seemingly safe and accurate URL.
Furthermore, we’ve all encountered fake emails and messages demanding urgent attention due to phishing attempts. Phishing extends beyond traditional email tactics, posing significant risks to businesses that neglect necessary precautions. A breach not only impacts finances but also damages a brand’s reputation and trust. The browser-in-the-browser attack is a phishing scam wherein sensitive user information is stolen by simulating a web browser window within another browser window.
This leads to identity theft as users encounter a deceptive pop-up window soliciting their login credentials for the website displayed in the previous browser window. To counter such attacks, companies must ensure robust security measures for both employees and customers. Now, let’s delve into the details of Browser in the Browser attacks.
What is a Browser In The Browser Attack?
When users opt for single sign-on (SSO) to access multiple interconnected applications on a website or web app, a malicious pop-up appears to extract sensitive information like login credentials. Unlike traditional phishing pop-ups during sign-in, a Browser in the Browser attack displays a URL that closely resembles the legitimate one. This enables cybercriminals to mimic a genuine domain by creating a web browser window within another browser. This attack capitalizes on users’ preference for SSO to avoid remembering lengthy credentials.
Given that users can’t easily differentiate between a fake and legitimate domain once a pop-up emerges, cybercriminals exploit the SSO preference, increasing the risk for businesses offering SSO across multiple apps. These businesses become susceptible to browser attacks targeting the interconnected browsers. To safeguard consumer information while providing SSO, companies must comprehend the associated risks and implement stringent security measures.
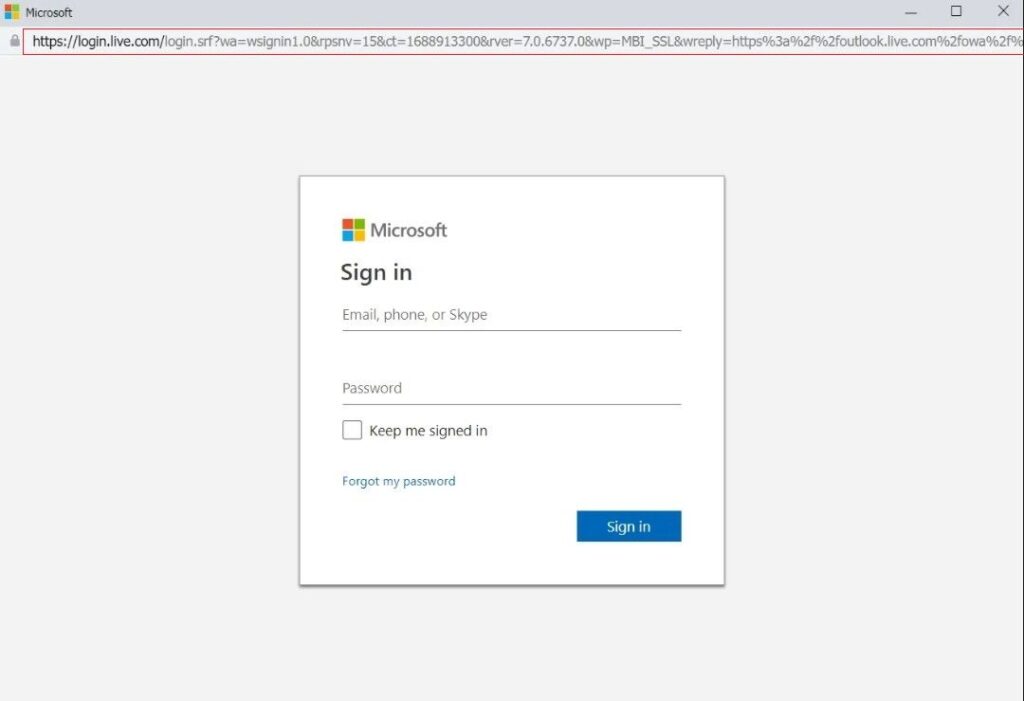
Detecting Real vs. Fake Login Windows
Despite their deceptive appearance, there are techniques to identify fake login windows. Genuine login forms function like browser windows – they can be maximized, minimized, and repositioned. In contrast, fake pop-ups lack this functionality. They can obstruct buttons and images within their boundaries, but only within those confines.
To determine if a login form is fake:
1. Minimize the original browser window from which the form appeared. If the separate login box also disappears, it’s a fraudulent site. Maintain a genuine window onscreen at all times.
2. Moving the login window beyond the parent window’s border indicates a fake. Authentic windows can cross over, whereas fakes cannot.
3. If the login form behaves oddly, like minimizing alongside the other window, halting beneath the address bar, or disappearing under it, refrain from entering credentials.
Preventing Browser-in-Browser Attacks for Businesses
Given the myriad benefits of SSO for businesses and consumers, avoiding it isn’t advisable. Preventing browser-in-browser attacks and associated risks involves implementing robust security layers alongside SSO.
Multi-Factor Authentication
Multi-factor authentication (MFA) is a multi-layered security system that confirms user identities for logins and transactions. Employing multiple authentication elements ensures account security even if one factor is compromised. Examples include smartphone app codes, personal security question answers, email-based codes, and fingerprints. Integrating MFA strengthens information protection against browser-in-browser attacks, with software and hardware tokens enhancing dual identity verification.
Risk-Based Authentication
To thwart browser-in-browser attacks, risk-based authentication (RBA) or adaptive authentication is a comprehensive approach. Authentication stringency adjusts based on potential system compromise, becoming stricter with higher risk. RBA employs varying levels of verification. Even in high-risk scenarios like browser-in-browser attacks, RBA adds an extra authentication layer, protecting user identities. Cloud-based consumer identity and access management (CIAM) platforms apply RBA, even when users employ SSO, curbing unauthorized access.
Zero Trust Architecture
Adopting a zero trust security concept entails strict verification before granting access to any device or individual, inside or outside the enterprise’s perimeters. Zero trust halts access until proper verification and trust are established. For instance, an individual or device demanding access must verify their identity to interact with an IP address, device, or storage.
Setting Up a Browser in the Browser Attack
In a Browser in the Browser attack, cybercriminals initially establish fake SSO authentication on a malicious website, luring targets to visit. This technique exploits SSO authentication. Once a target registers using fake SSO, the attacker stores the credentials in their database. Despite the seeming complexity, phishing frameworks and webpage templates automate the process. Templates replicating Google, Facebook, and Apple login pages are already available, as published by security researchers.
In conclusion, the evolving landscape of cyber threats demands constant vigilance and proactive measures to safeguard sensitive information. As cybercriminals continually innovate new techniques to deceive users, it is crucial for individuals and businesses alike to stay informed and adopt robust security practices. The Browser in the Browser attack exemplifies the sophistication of modern phishing tactics, where even seemingly legitimate URLs can be used to trick users into divulging their credentials.
Sri Lanka Computer Emergency Readiness Team | Coordination Centre
- Hotline : 101
- +94 11 269 1692
- Room 4-112, BMICH, Bauddhaloka Mawatha, Colombo 07, Sri Lanka.
- General inquiry: cert@cert.gov.lk
- Security incidents: incidents@cert.gov.lk
- Social media incidents: report@cert.gov.lk



